[dev.icinga.com #3715] Revamped credential and permission system for the data #1032
Comments
|
Updated by ossmon on 2013-02-20 06:58:57 +00:00 Hi, |
|
Updated by mfriedrich on 2013-02-25 08:27:59 +00:00 hmmm, if applicable, i'd like to discuss a backport into current 1.8 tree when this is finally tested for the 1.9 tree. |
|
Updated by ossmon on 2013-03-21 14:15:57 +00:00 Hi Markus, when do you think that you will have a version to be tested ? |
|
Updated by mfrosch on 2013-04-22 17:50:47 +00:00 I've integrated and pushed the grouped aggregation of credentials to feature/credentials-3715-step2 @mhein: We still need to implement this kind of grouping for the Legacy Api stuff. And many testing... |
|
Updated by ossmon on 2013-04-22 19:25:09 +00:00 Hi Markus, should I test your git version or should I wait for more time ? |
|
Updated by mfrosch on 2013-04-23 06:25:23 +00:00 Hey, any test is welcome. It would be great to get your feedback, especially in terms of your use of permissions! |
|
Updated by ossmon on 2013-04-23 07:48:02 +00:00
Hi Markus, 2 cases: In the config exist only one host with a custom variable VAR1 and one of its service has also the same custom variable VAR1.
=> OK
=> The user see many hosts and services (not only one) |
|
Updated by mfrosch on 2013-04-26 10:02:55 +00:00
The branch feature/credentials-3715 has been merged into next. I think the credential system should now work as intended, please test and also have a look if the detail tabs of a host or service to see if the LegacyApi permissions work as well. @ossmon: Please test ;) @tommi / dnsmichi: Could you try the latest changes in a Oracle environment with some credentials? Thanks |
|
Updated by ossmon on 2013-04-26 11:31:09 +00:00 It works fine now ! Congratulation ! |
|
Updated by Tommi on 2013-04-26 18:53:22 +00:00 Howto test? Which settings/configs are required? |
|
Updated by mfriedrich on 2013-04-26 18:56:28 +00:00 set users to special permissions - e.g. hostgroups or servicegroups, and then check if they can only see those. if you have custom vars defined on services or hosts, add the permissions on the user admin panel as well for custom vars, and verify that the user may only see those. last but not least, test mixed permissions, like multiple groups, cvs, and such. should work with all 3 rdbms. |
|
Updated by Tommi on 2013-04-28 16:37:02 +00:00
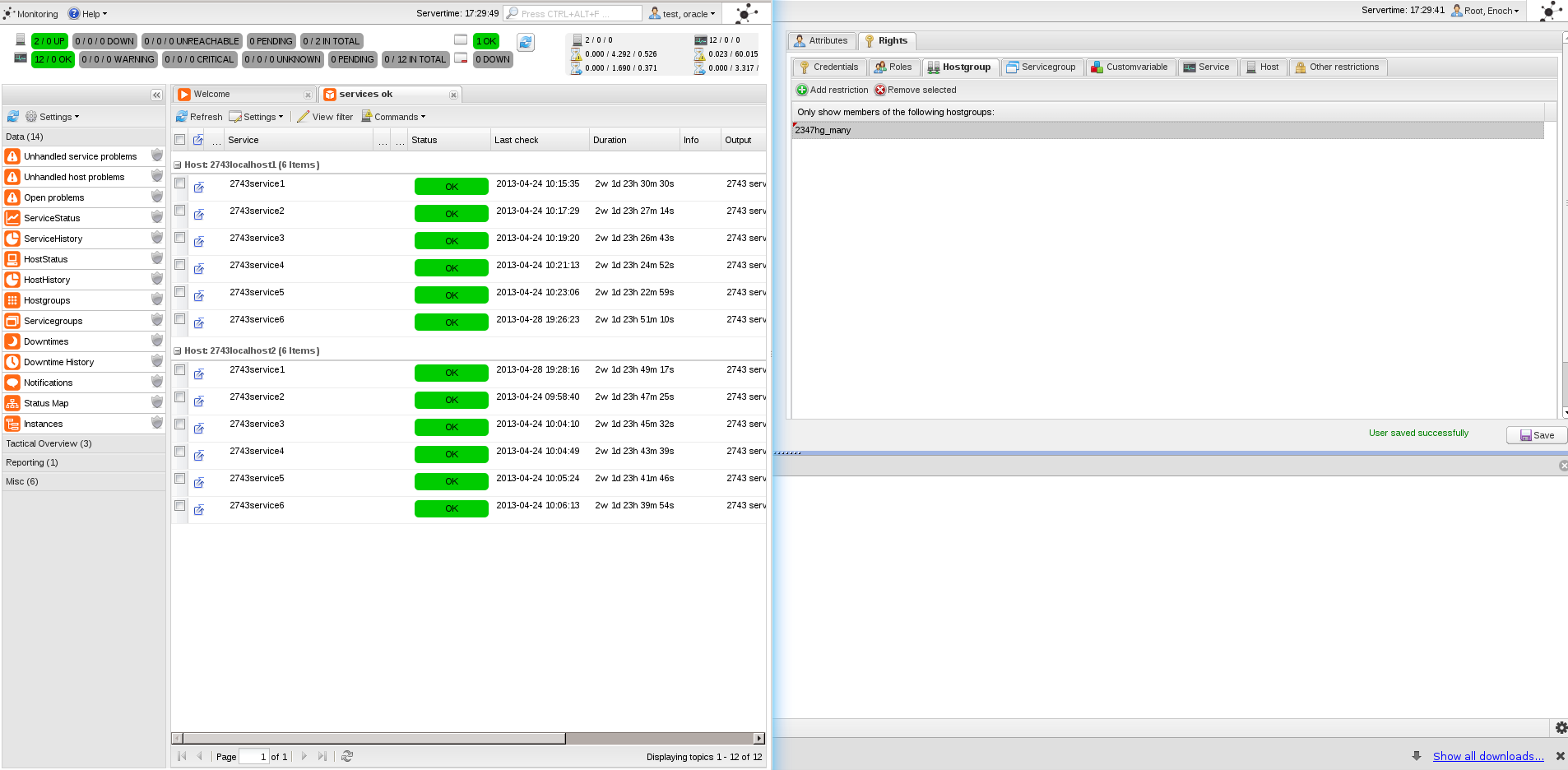
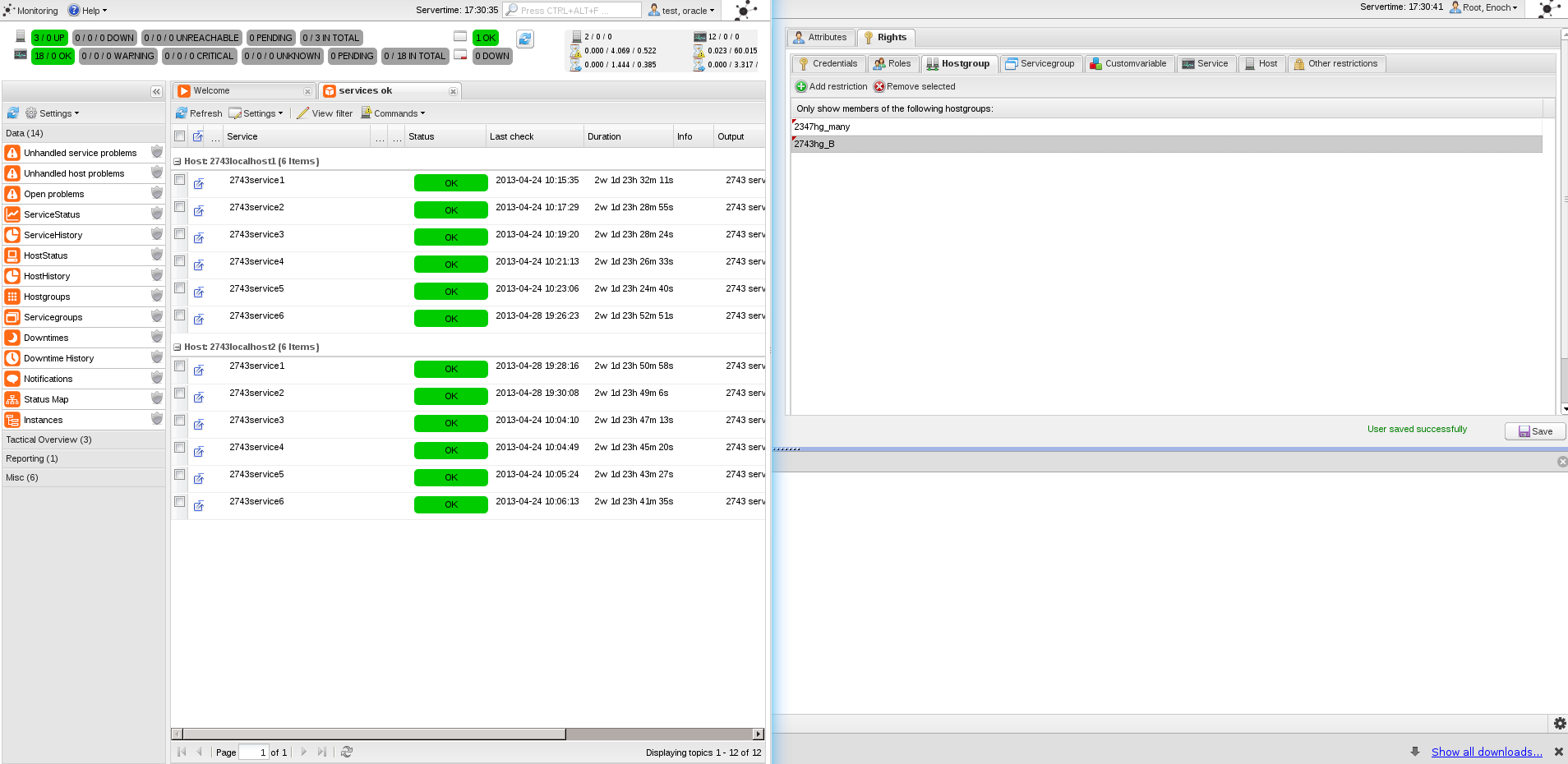
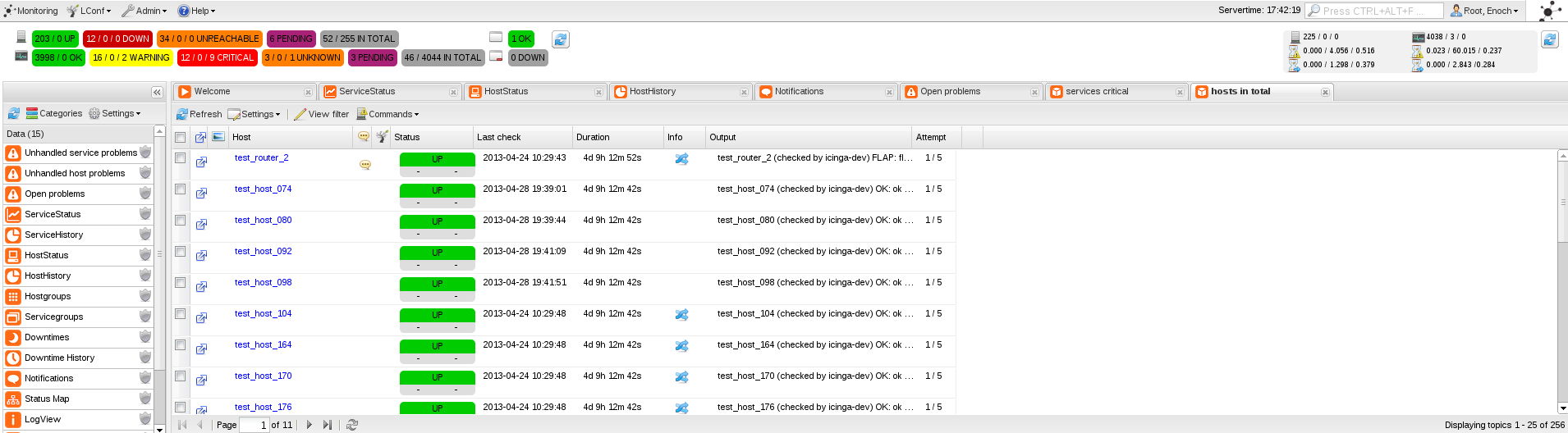
just did such tests after upgrading to the current next branch. Added a new user (there is another small issue i logged in #3999) and add restriction to one hostgroup, one servicegroup and one (host)custom variable value. This should match for exact one database instance and hiding all others. First off all, no database syntax errors appeared while running my tests. But the Screen contents aren't as expected. It doubled the numbers of services and host and shows services which are not matched with the supplied custom variables when using the restricted user. Just added a few screenshots of this issue |
|
Updated by mfriedrich on 2013-04-28 17:34:51 +00:00
looks like the distinct fix does not work anymore for the status cronk. first of my test row with oracle: 1 hostgroup, and more. single hostgroup contains 2 hosts which relate to 6 services. that's totally fine. (left is iceweasel with the test session, right is chromium with root permissions) when i add yet another hostgroup, which also contains both hosts, the display in the grid stays the same (12) but the status cronk counters are wrong. they sump up to 18 being ok, which is not shown in the grid. the correct number is still 12. first conclusion - the status cronk counter does not know about the new privileges. |
|
Updated by mfriedrich on 2013-04-28 18:45:20 +00:00 I've created a dedicated test config for that, used from within the core's test config (which i keep writing for issues and their resolval / regression testing. |
|
Updated by mfriedrich on 2013-04-28 19:38:16 +00:00 further oracle tests on the issue with
are collected in #4002 as seperated issue. |
|
Updated by mfriedrich on 2013-05-04 12:20:01 +00:00 further oracle distinct issues are collected in #4048 |
|
Updated by mfriedrich on 2013-05-06 08:11:40 +00:00
for the initial issue, i consider this resolved and working. thanks for the hard work on this, further bugs may be collected and fixed on the bugfix 1.9.x tree. just make sure to commit often and even more often to allow easier git flowing ;) |



This issue has been migrated from Redmine: https://dev.icinga.com/issues/3715
Created by mfrosch on 2013-02-19 14:43:04 +00:00
Assignee: mfrosch
Status: Resolved (closed on 2013-05-06 08:11:40 +00:00)
Target Version: 1.9
Last Update: 2013-05-06 08:11:40 +00:00 (in Redmine)
We are working on some major credential changes for 1.9 and like to her feedback for what we are doing.
Please comment below this issue, I'll refer and maybe also close other issues in favor of this one.
Most of the work and testing will be done by me and Jannis.
Feel free to comment and add suggestions or questions.
Git branches we are working on:
feature/datapermissions*
Cheers
Markus
Step 1
Step 2
Step 3
The whole idea
The whole credential system will consist of 2 pools of credentials:
The rights of a user will be aggregated and inherited from every target that is set on the user directly or a role he is member of.
The permission to grant rights by matching contactname and groups will be working as intended (some fixes are necessary), and it will be working in addition to other credentials the user might have.
A permission filter (in the end of our work) should work like this:
After Step 1 (temporary):
The final idea is to build a aggregate of all permissions a user has, but requiring him to match a host and a service credential.
Attachments
Changesets
2013-04-25 11:59:18 +00:00 by mfrosch 1335fd3
2013-04-25 13:04:10 +00:00 by mfrosch 9dc7513
2013-04-25 13:05:57 +00:00 by mfrosch f8f035e
2013-04-25 13:38:49 +00:00 by mfrosch 4a78f84
2013-04-26 09:53:43 +00:00 by mfrosch 0a496b0
2013-04-26 09:54:15 +00:00 by mfrosch 4e7c0f7
2013-04-30 15:44:21 +00:00 by mfrosch b982b4f
Relations:
The text was updated successfully, but these errors were encountered: